Ligolo-Ng : Pivoting use cases
Ligolo-ng is a simple, lightweight and fast tool that allows pentesters to establish tunnels from a reverse TCP/TLS connection using a tun interface (without the need of SOCKS).
Ligolo-Ng is a unique pivoting tool that allows you to create VPN-like tunnels, enabling direct interaction via target IP addresses instead of using socks proxies. With an interactive CLI interface, you can easily jump from one agent to another without any hassle.
Ligolo-Ng has two parts: a proxy that acts as a C2 interface to locate and select your targets, and also enables listeners on the target machine; and an agent that you implant on the target machine to initiate the VPN connection from the target machine to the attacking machine.
The agent does not require higher privileges on the target machine, so you can use a classic reverse shell to simplify any attacking methodology. With Ligolo-Ng, you can run any tool from your attacking machine against a target machine by closing the network gap between layers of networks.

Setting up Ligolo-ng
Creating a Tun Interface
Once you have added the TUN Interface and the sub networks that you want to access from the attacker PC, you can now launch ligolo proxy on the attacker PC and the agent on an already compromised host in the internal network.
Connecting to a Ligolo-Agent
Agent Binding/Listening
Agent Binding/listening on ligolo allows you to capture reverse shells from an internal network and forward it through the ligolo connection. You can then launch a netcat/pwncat-cs from the attacking machine seamlessly, give you the impression as if you were already in the target network.
Ligolo-Ng Pivoting Tutorials / Use Cases
1. Accessing the Target Network
Once a connection is establised on the Public Facing Server that is in the Target Network via a reverse shell, it is possible to access/enumerate or exploit any vulnerabilities against a different target in the same network trough ligolo (such as a DMZ) or a target that is in a neighbouring network (in the case of a non-segmented network). This allows an attcker to use their very own tools from the attacking machine.
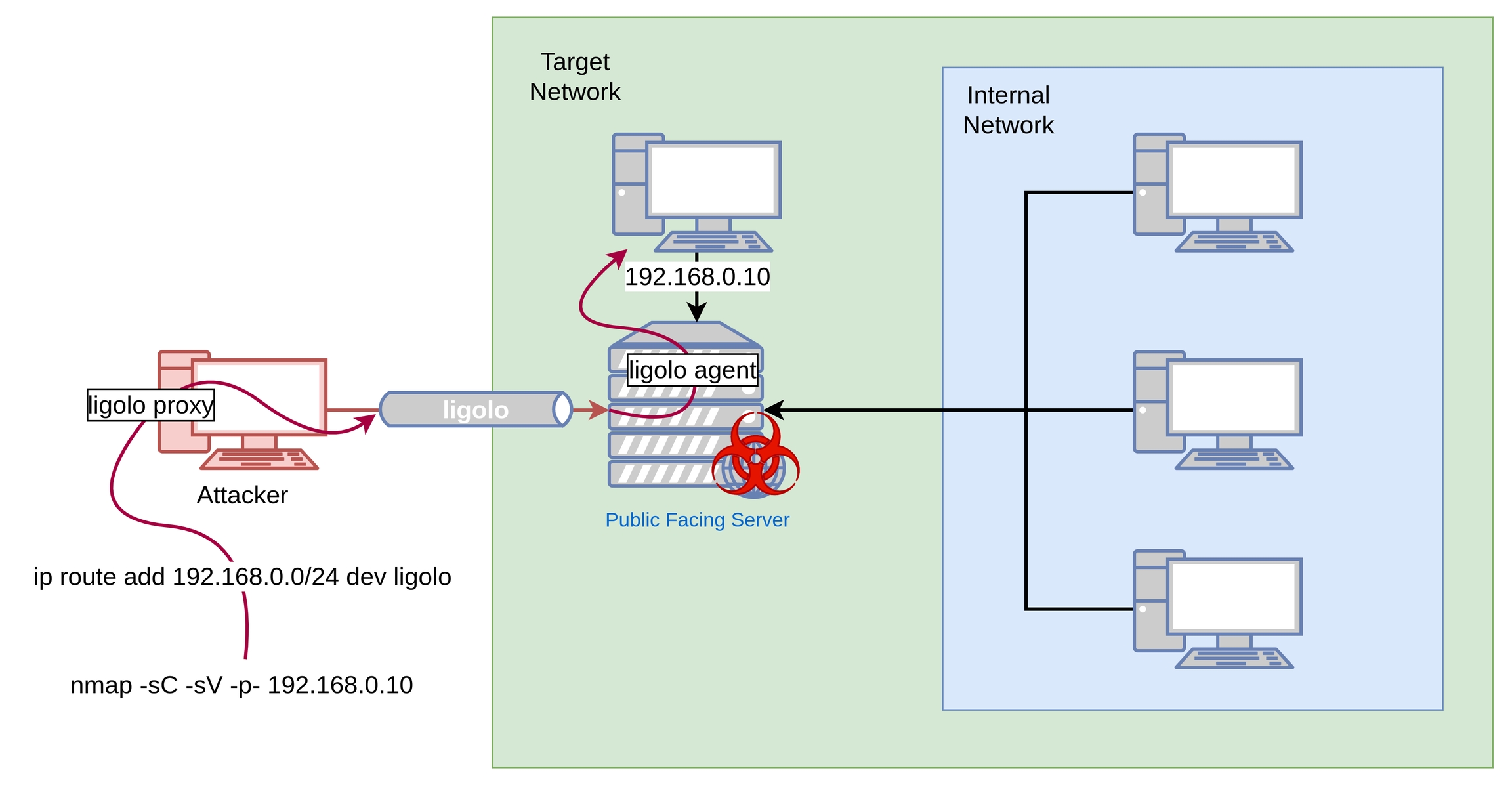
1.1 Forwarding a reverse shell from the Target Network
Using the Ligolo's Agent Binding/Listening feature, it is possible to recieve a reverse shell connection from a target (in the Target Network) that does not have direct access to the attacking machine (ie. an internet/WAN access). An agent in a compromised server that can communicate with the target can also act as a listner, thus allowing to forward reverse shells through the ligolo tunnel back to the attacking machine.
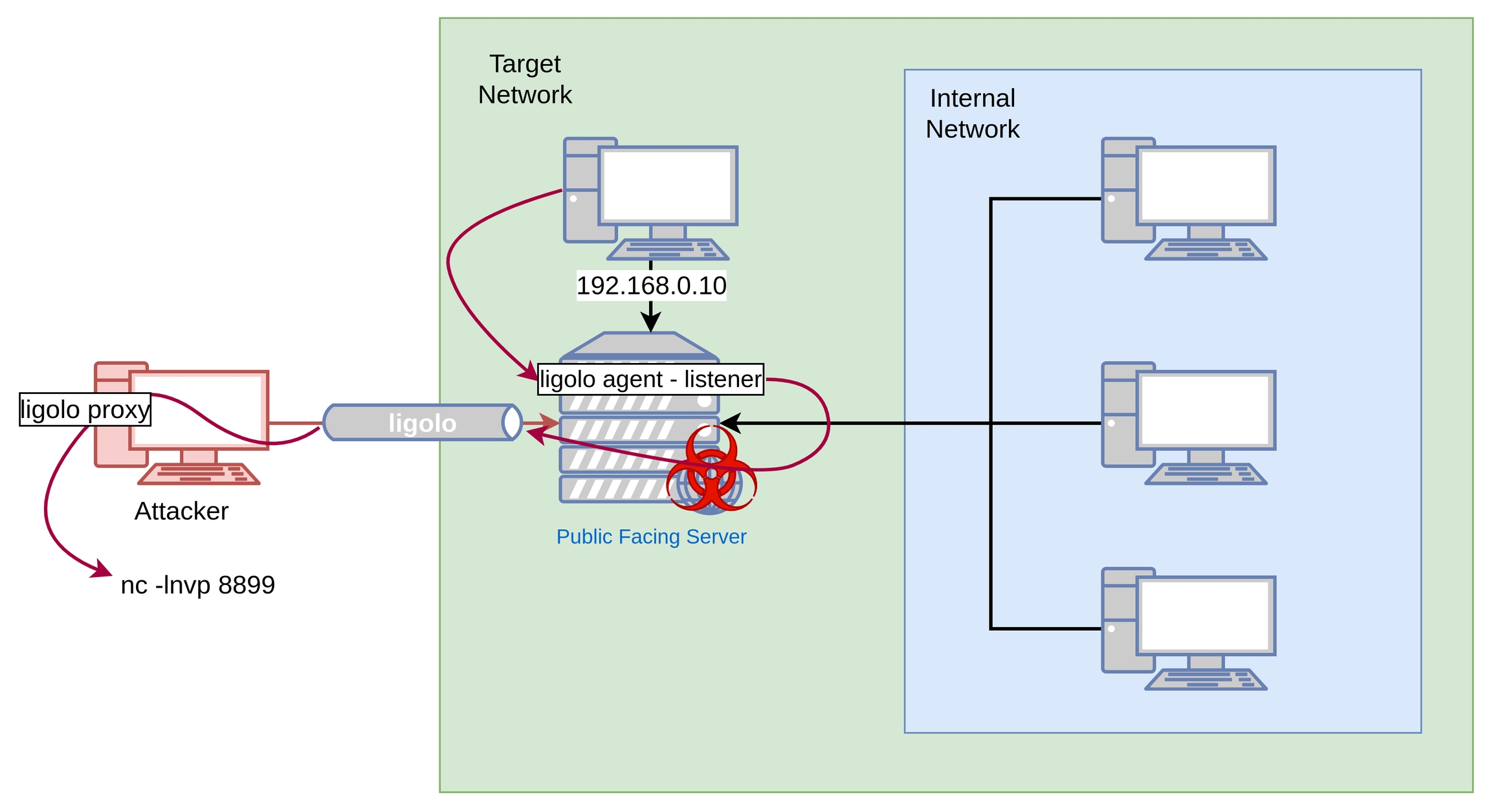
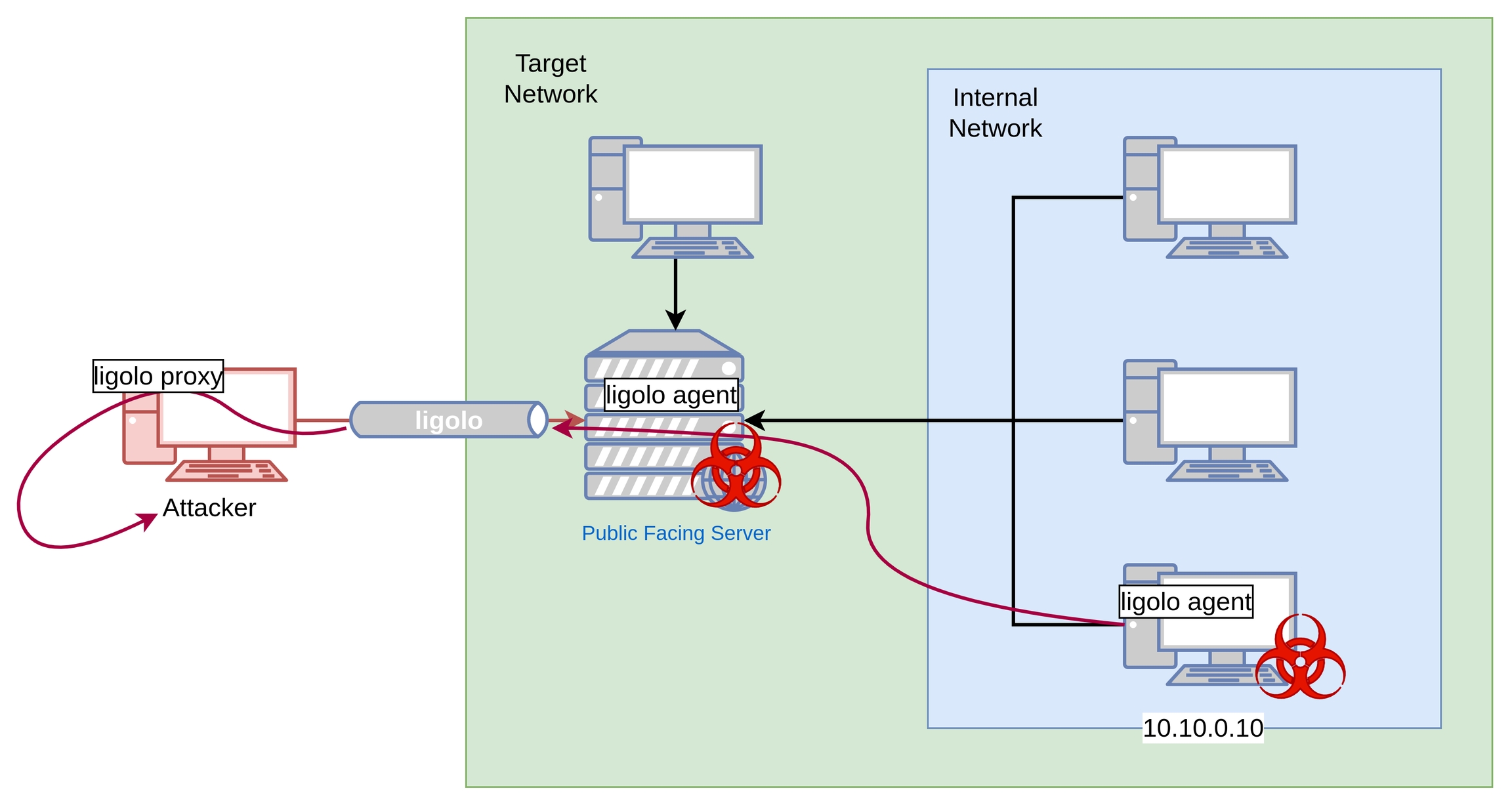
1.2. Accessing the Internal Network
It is also possible to implant ligolo agents into deeper levels of the network in an organization inorder to compromise additional servers/devices. This follows the simmilar steps that were described for the Public Facing Server. However, this requires once again a reverse shell in the Internal Network or other sorts of foothold as a low privileged user in the internal network.
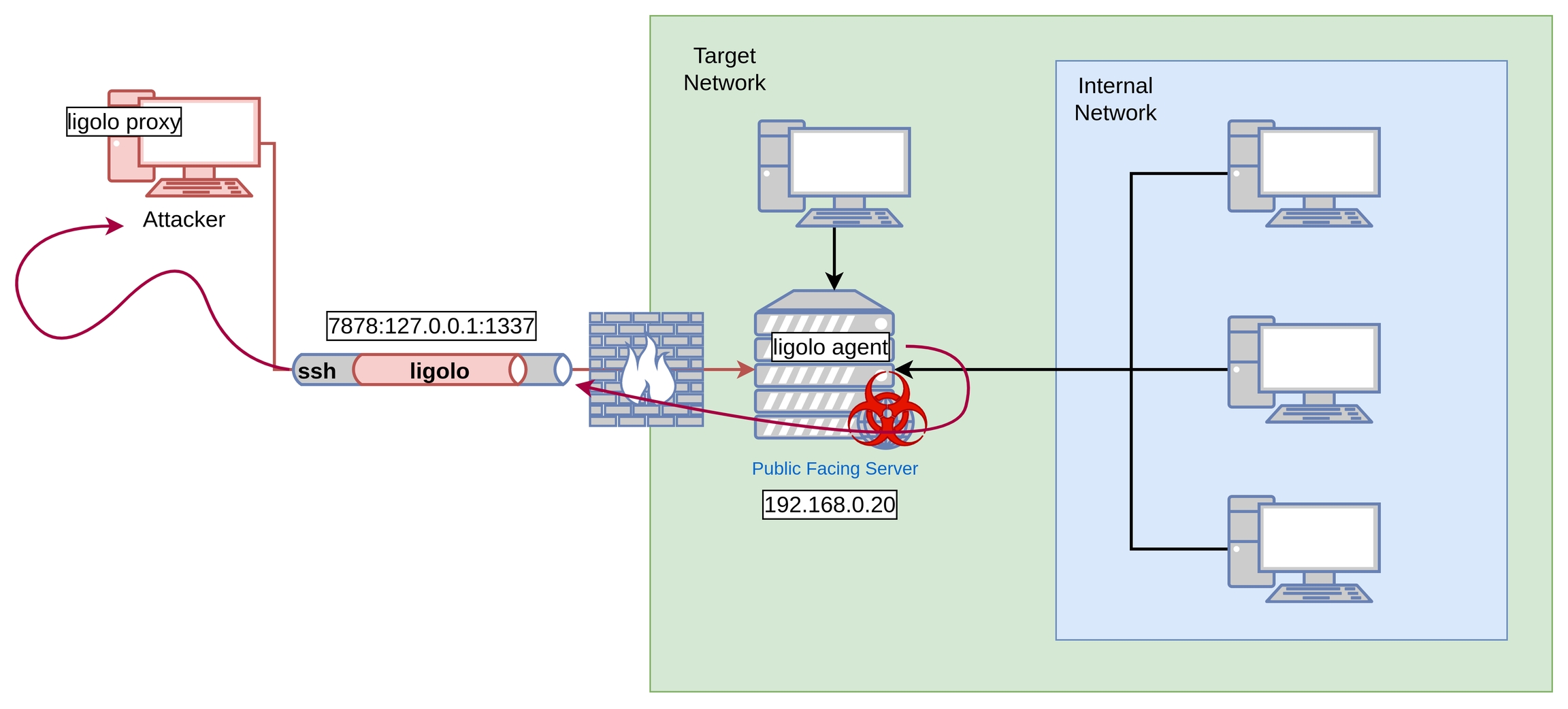
2. Pivoting Ligolo-Ng with SSH access
In the case where the Target Network as well as the Internal Network has no possibility to contact the attacking machine but via a SSH connection, it is possible to initiate a connection from a ligolo agent implanted in the Public Facing Server via a SSH Reverse tunnel.
To do this, you will first have to initiate a Reverse SSH Connection. This is mainly because the ligolo proxy always listens to connections that are first initiated by the ligolo agent. A reverse ssh connection will allow us to open a port within the Public Facing Server and whatever that connects to that perticular port will then be tunnled trough the SSH connection.
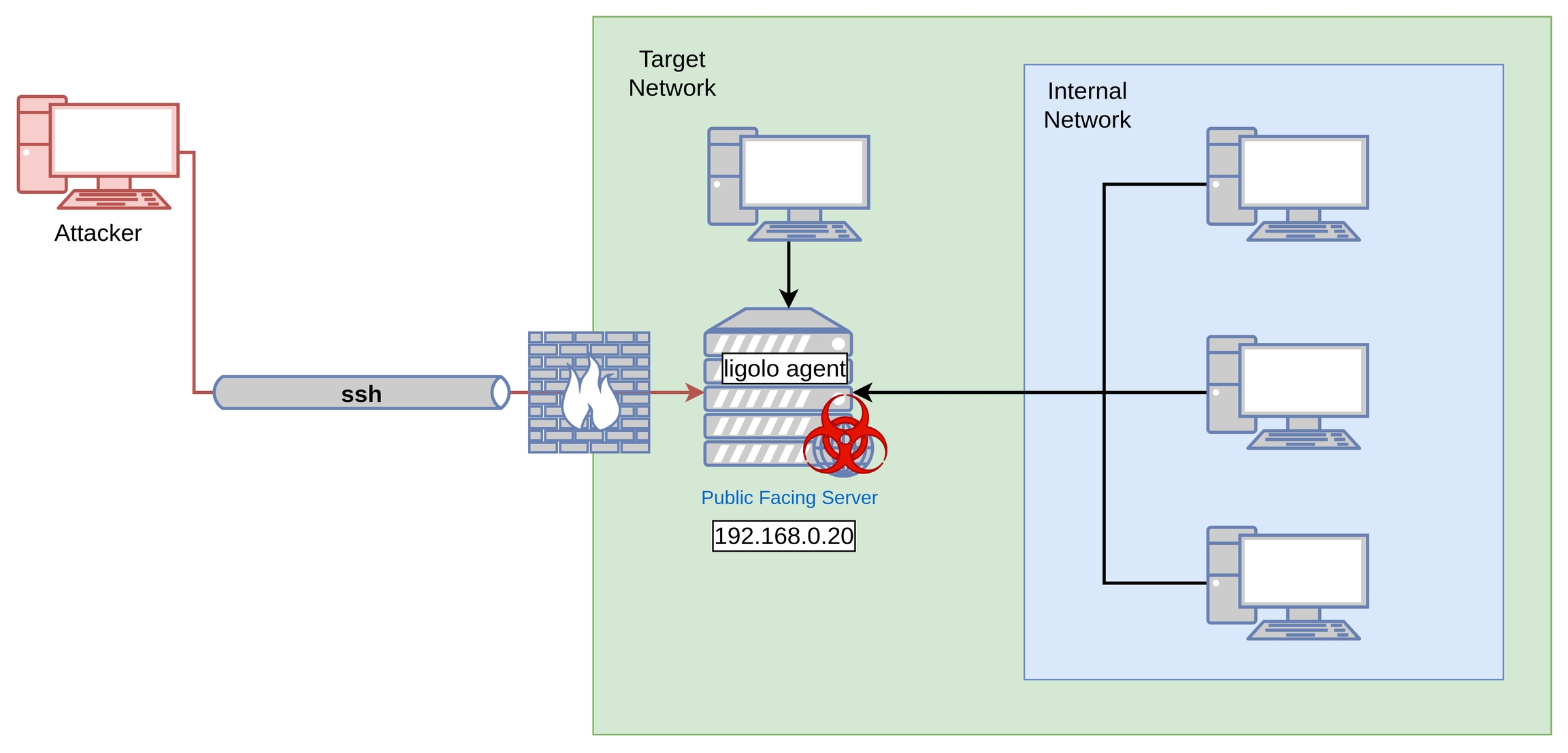
Once the ssh tunnel is established, now you can transfer the ligolo agent and run the ligolo agent from the target server, simmilar to the steps shown above..
2.1 Pivoting Ligolo-Ng with SSH access + SOCAT
In order to avoid initiating multiple SSH connections per ligolo agent connection, you can tunnel these connections through a single SSH connection. To achieve this, we will be using the tool socat.
Last updated
Was this helpful?
